Nowadays, not even simple passwords like 123456 are easy to break. With modern technologies and the power of computer hardware, breaking strong passwords including special characters and symbols is only a matter of time. More specifically, with “Dictionary” attacks, simple passwords can be break just in a second. For stronger passwords, just weeks or few months at most is enough thanks to “Brute-Force” attacks. Many companies require users to change their passwords every few months. ISO 27001, for example, also requires applying this policy. This is quite annoying for our users to remember all their new complex passwords, so some just write down their passwords, hide them under the desk or simply stick them on monitors which then become a big risk instead of a security enhancement.
In contrast to static passwords, One-time passwords, which are changed twice every minute, are not vulnerable even with replay attacks. That means a potential intruder who manages to record an OTP that was already used to log into a service or to conduct a transaction will not be able to abuse it, since it will no longer be valid.
Now instead of remembering a complex password, our users can simply install a software token on their phone or receive an SMS OTP upon request, compile it with their secret static PIN, the password security break has been solved on those systems which applied Multi-factor authentication.
Unfortunates, not all the system have build-in multi-factor authentication function, but as many of them ready to intergraded with RADIUS or LDAP, we choose RADIUS as our solution below:
1/ User -> PIN + software token -> server -> radius -> OTP module
2/ User -> PIN -> server -> radius -> OTP module -> sms token -> user -> PIN + sms token -> server -> radius -> OTP module
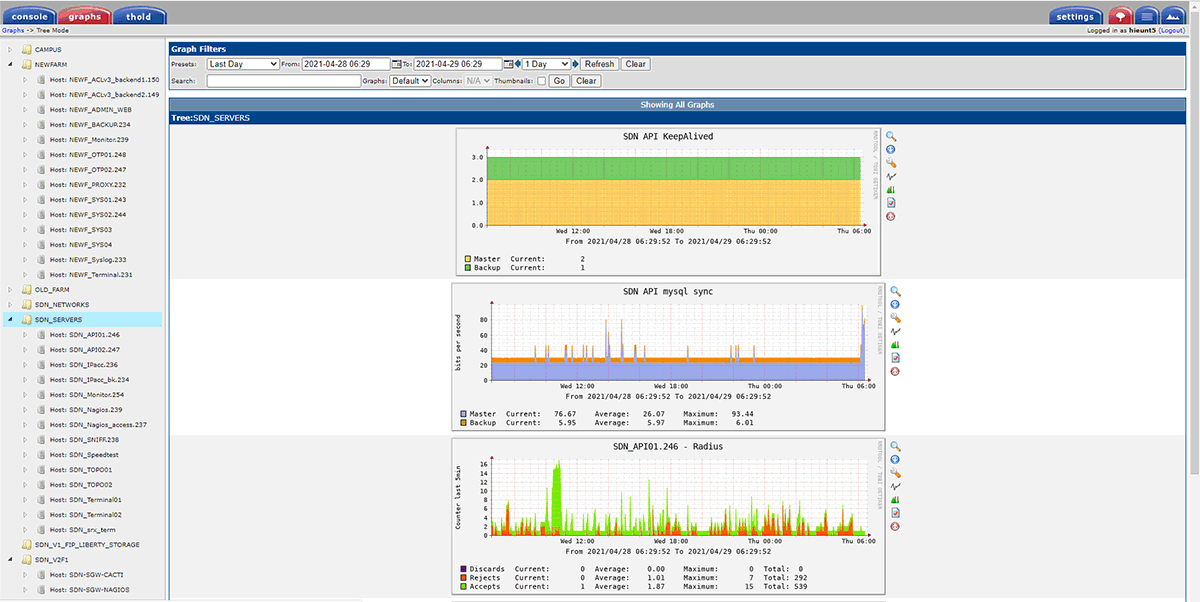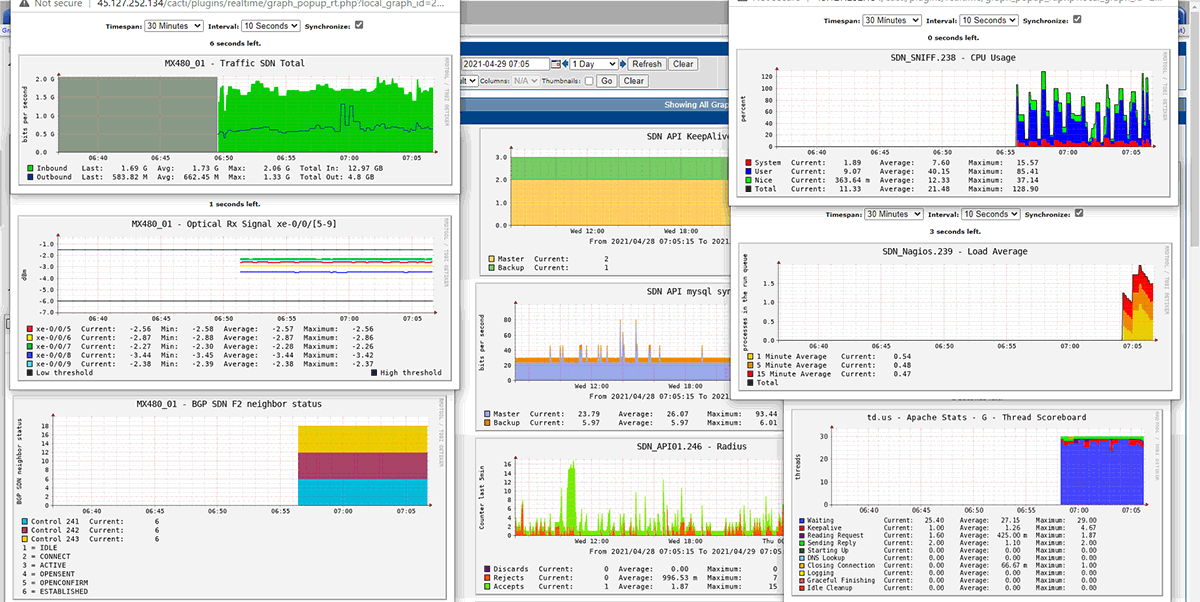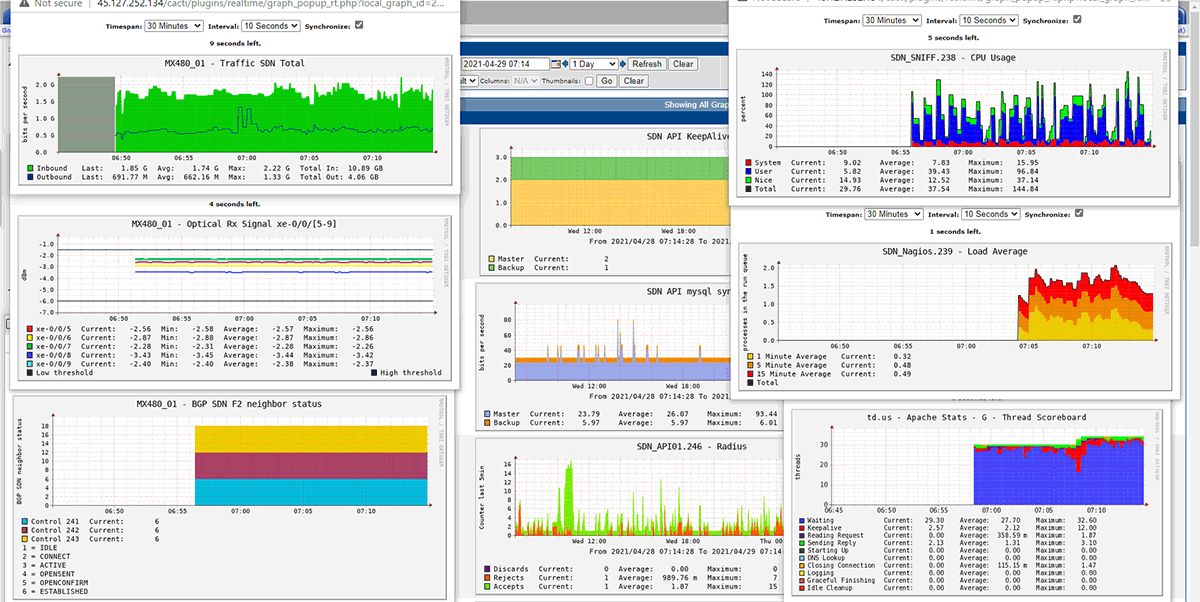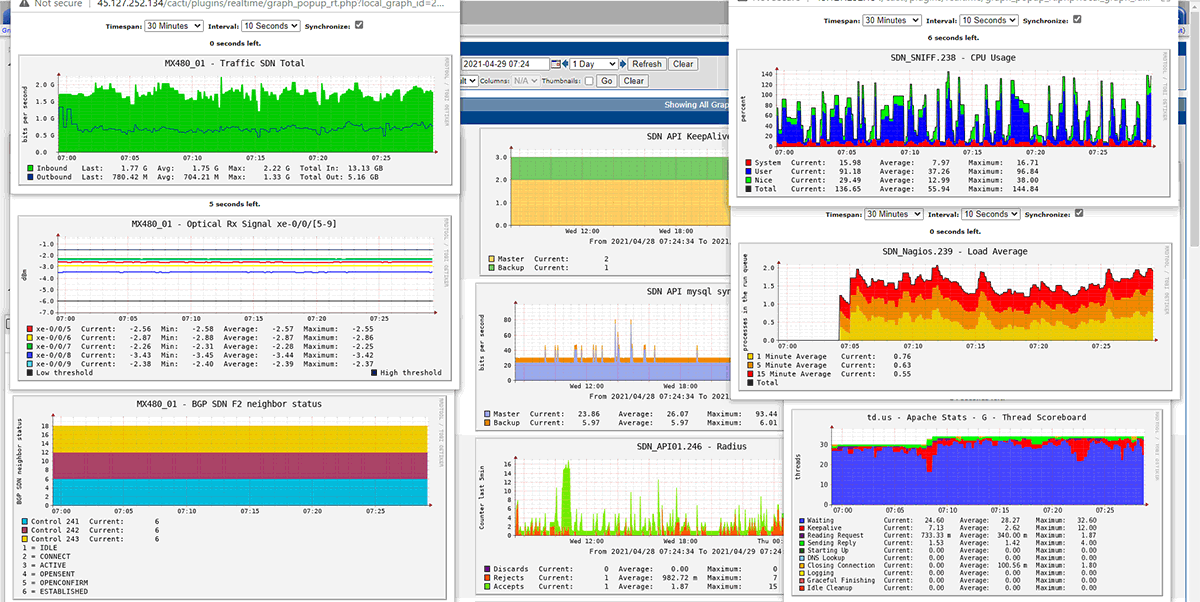
We did successfully intergrade our application and devices listed below with OTP, they are working well in the production environment for years without any complaint from our clients
– Linux sshd servers: with pam_radius module
– Cisco network devices 28xx, 3750, 4507, 6509, 7609: with radius and TACAS+
– Cisco ACS
– Juniper network devices : EX4200, EX4300,EX9200, QFX5100, MX80, MX480, MX960, SRX3600, SRX5600, SRX5800
– Apache web servers 2.2 and 2.4: required LinOTP_auth module installed on the server
– SoftEther VPN server: using external radius authentication.
– Our software development team they also happy to use radius client library instead of storing a static password database.
If your company have not got OTP/Multi-factor authentication yet and you interested in this solution, please contact and I will be pleased to help